Why coronavirus scammers can send fake emails from real domains
Organizations like the WHO could prevent domain spoofing, but many don’t.
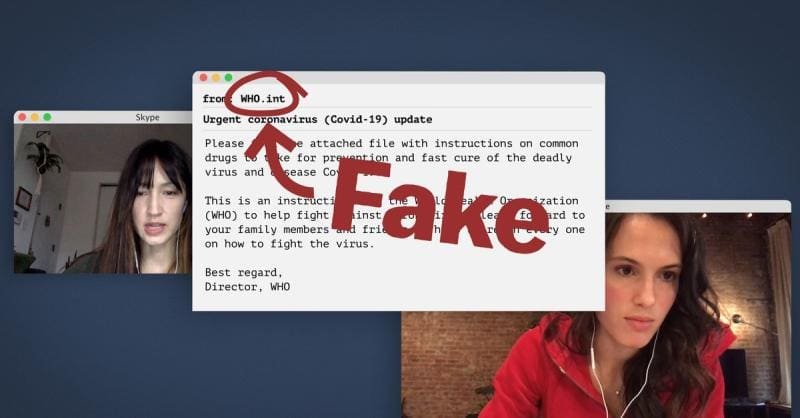
On March 18, an email went out from the World Health Organization soliciting donations for its Covid-19 Solidarity Response Fund, to support WHO’s work tracking and treating the novel coronavirus. The sender address was “donate@who.int,” and who.int is the real domain name of the organization.
But the email is a scam. It was not sent from the WHO, but from an impersonator looking to profit off our tendency toward generosity during a global crisis. Fortunately, the attacker revealed themselves by asking for donations in bitcoin.
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/19864479/donate_response_fund.jpg)
This is just one of many fake emails that have spoofed the WHO’s domain name during the coronavirus pandemic. Some are addressed from Tedros Adhanom Ghebreyesus, the director-general of the WHO, and carry attachments that can install malware on the victim’s device. Others announce a coronavirus cure that you can read all about in the attachment. They each appear to be sent from a who.int email address.
If it seems like it shouldn’t be this easy to impersonate a leading global health institution, you’re right. As we outline in the video at the top of this post, there is a way for organizations and companies to prevent spoofing of their domain, but the WHO hasn’t done it.
“One of the things that a lot of NGOs and nonprofits don’t necessarily understand is that email is a very open protocol by design,” said Ryan Kalember, who leads cybersecurity strategy at Proofpoint.
That “open protocol” means that the email transmission system itself doesn’t verify the identity of senders. Instead, senders and receivers have had to organize voluntary authentication methods: Domain owners can adopt an ID system, and email providers can check for for those IDs. But participation has not been universal on both sides.
“There are just so many organizations that don’t authenticate their mail. So if you are interested in tricking someone, that becomes an incredibly useful vector to do so,” said Kalember.
There are three main pieces of jargon to learn…